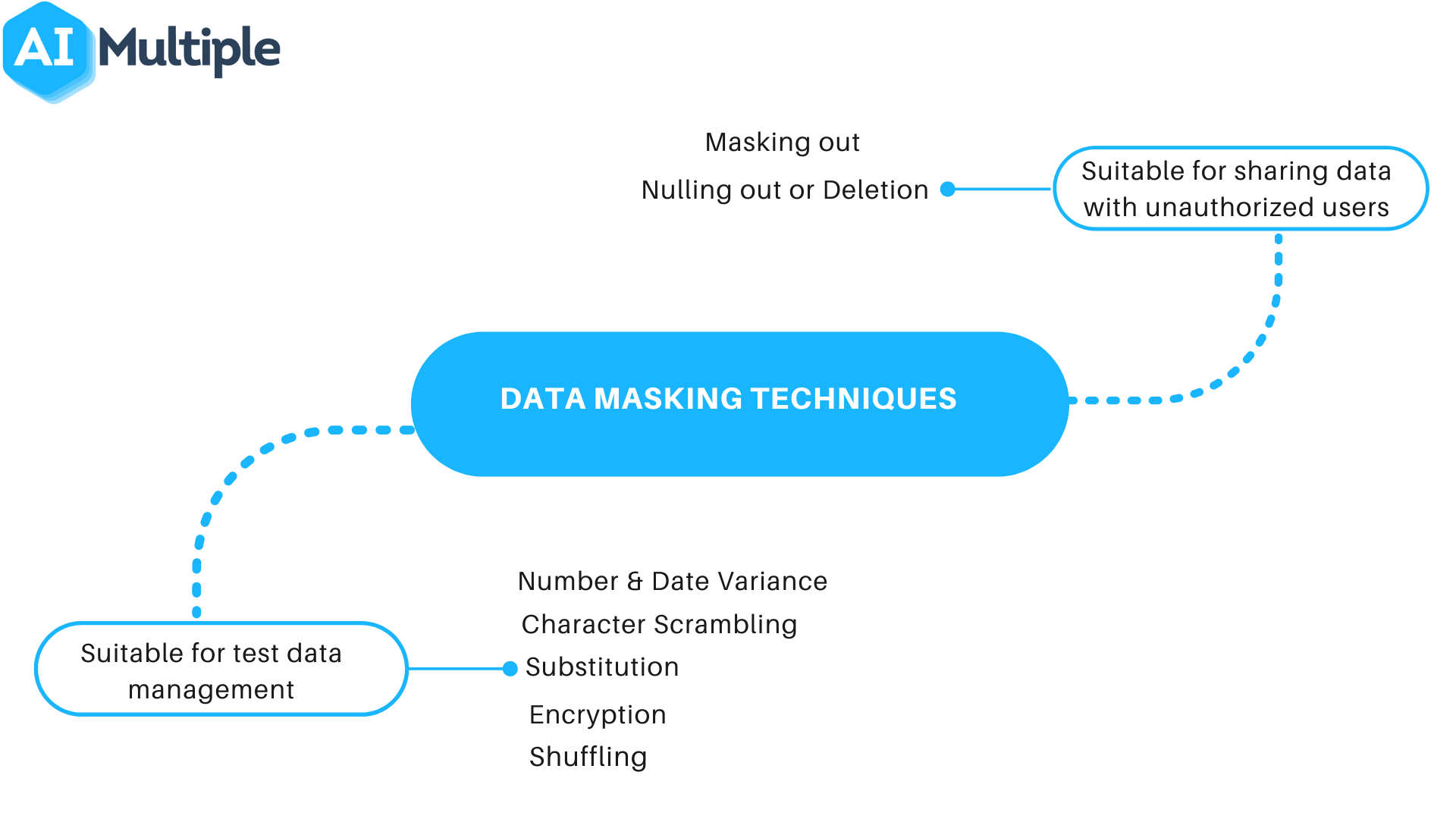
Data Masking Counter Attack to Identity Theft Paul Preston Data Masking: Counter Attack to Identity Theft. - ppt download
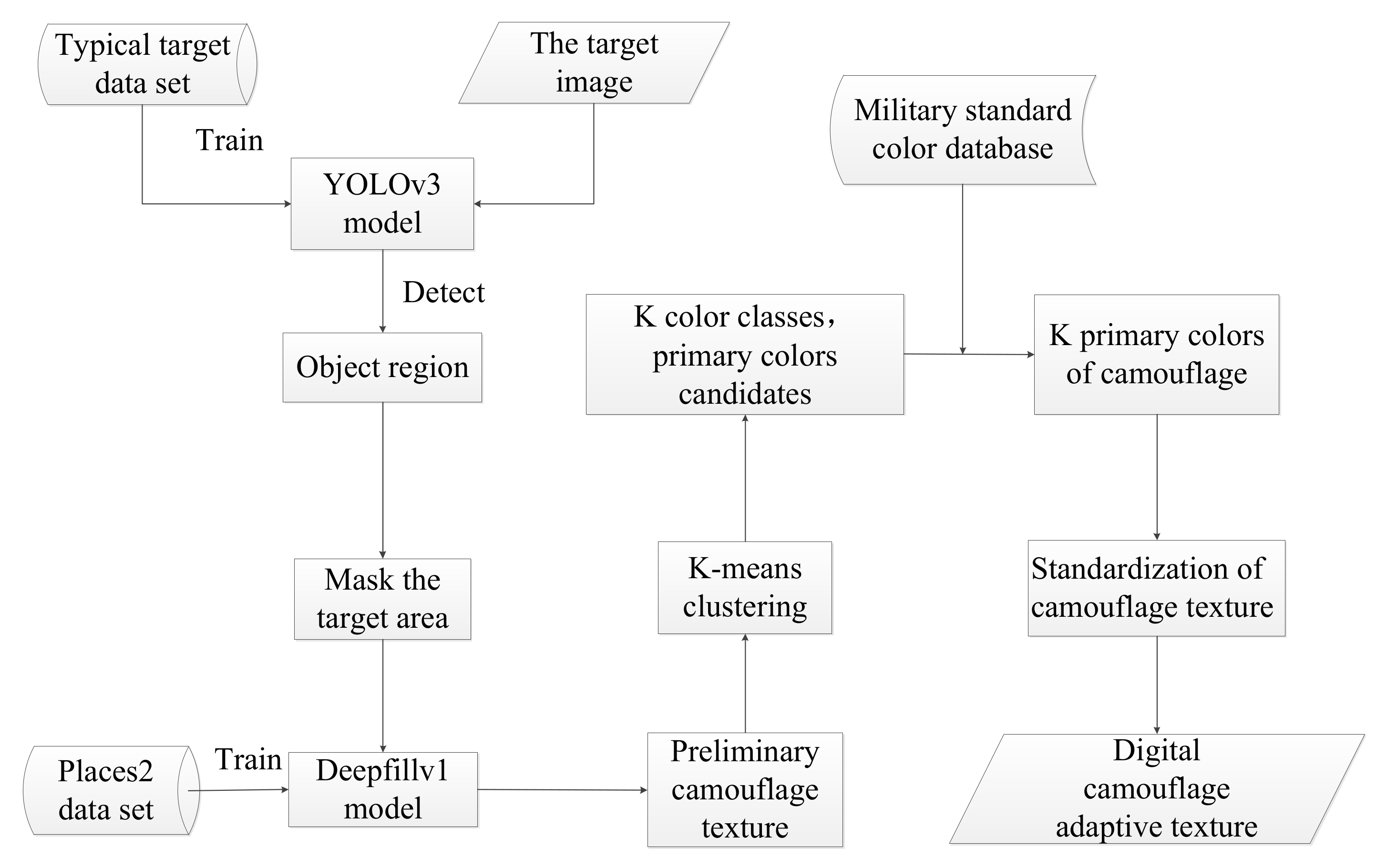
Applied Sciences | Free Full-Text | Fast Self-Adaptive Digital Camouflage Design Method Based on Deep Learning

Data Masking Counter Attack to Identity Theft Paul Preston Data Masking: Counter Attack to Identity Theft. - ppt download